Some data allegedly from the Georgia Board of Education was offered for sale on a hacking-related forum last week. But were they really from the state board of education? After DataBreaches started asking questions, the listing seems to have been removed.
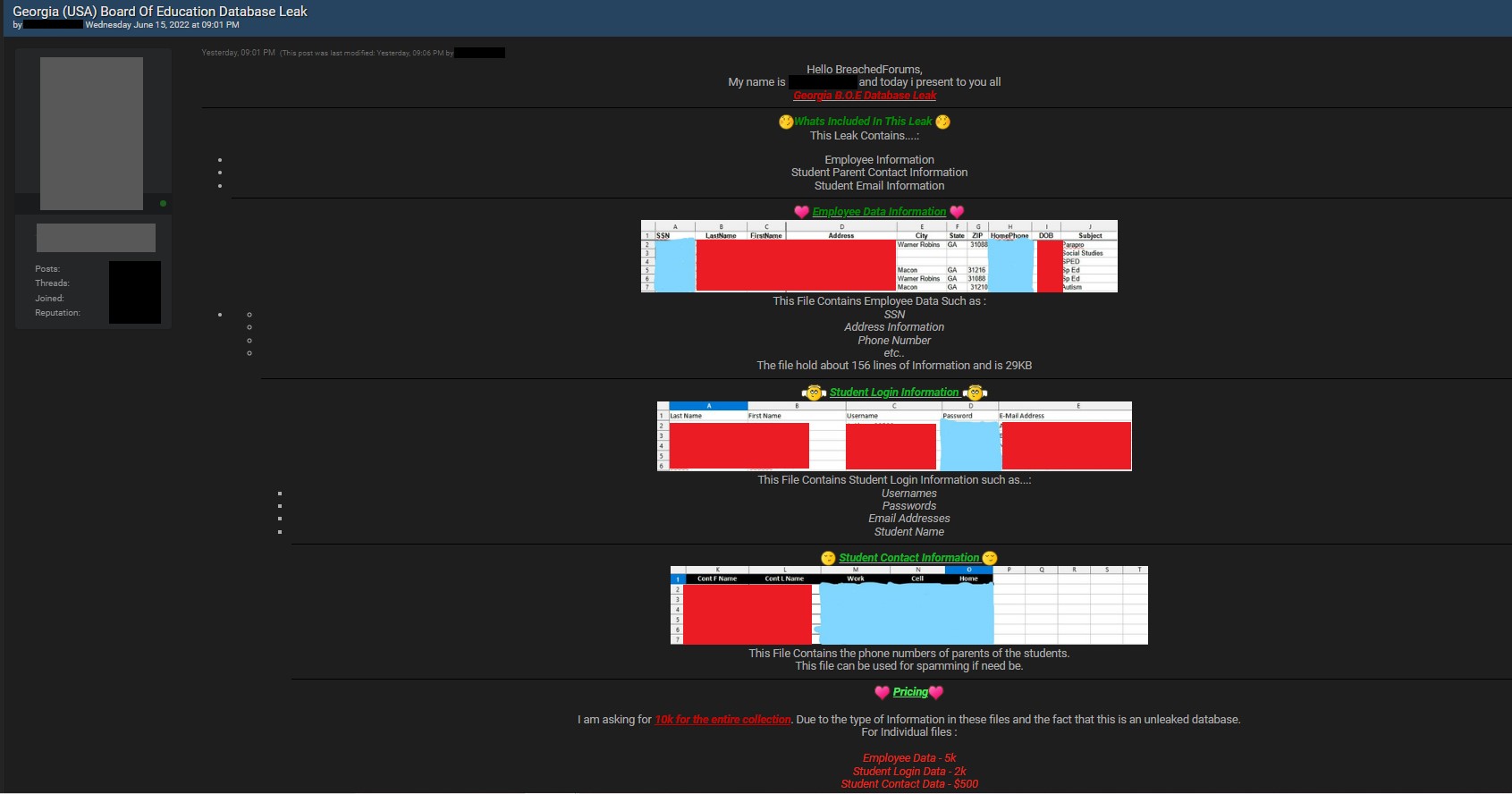
Last week, DataBreaches.net spotted a listing on a hacking-related forum that offered what was described as the personal information of students, parents, and employees from the “Georgia (USA) Board of Education.” The seller, a new member of the forum, claimed to have some employee data that included 156 rows with employees’ Social Security numbers and phone numbers. They also claimed to have student login data with names, email addresses, usernames and passwords, as well as yet other data with parental contact information.
Are These Data Really From a State Database?
Inspection of the sample data posted by the seller failed to reveal any data that actually pointed to the Georgia Department of Education (GaDOE) or the Georgia Board of Education (GaBOE).
In the screencaps provided by the seller as a sample, the only email addresses provided relate to hcbe.net, which is the Houston County Board of Education (HCBE) in Perry, Georgia.
When a forum member asked for more information about the amount of data, the seller responded that there were 5,166 lines in the Student Contact Information and 1,962 lines in the student login information data. That is not a lot of data for what is allegedly a state database. It is not even a lot of data for a county database or a single school’s database if compiled over years. The listing offered no explanation for why there was so little data offered for sale.
Using Google, DataBreaches was able to confirm that there are (or were) HCBE employees with the names listed in the employee screencap, although DataBreaches has not yet been able to confirm whether those are current employees or past employees. DataBreaches was also able to find adults in that area whose names matched the names of adults listed as parent contacts for students.
When contacted by DataBreaches with questions as to whether the data were really from the state or from HCBE and whether the data were recently hacked or scraped, the seller declined to answer questions about where the data came from and would only say that the data had been acquired “recently.” Follow-up questions also produced no new answers, and the seller indicated none would be forthcoming.
Contacting the State and County
On June 16, DataBreaches reached out to HCBE via email and phone calls to their Superintendent’s Office and IT department. In addition to a detailed email and a detailed voicemail pointing IT to the email and leaving this site’s contact information, DataBreaches spoke to the Superintendent’s assistant, who seemed to understand the importance of the call.
HCBE did not reply to the calls or the email, though. Nor did they reply to a second email sent on June 17.
On June 18, DataBreaches sent an email to the Georgia Department of Education to ask Nicholas Handville, their Chief Data and Privacy Officer for Technology Services, whether the state DoE had recently had any breach or data security incident.
No reply from the GaDOE has been received.
On June 19, DataBreaches sent an email to the Georgia Board of Education to ask them if the GaBOE had recently had any breach or data security incident.
No reply has been received.
At this point, then, the data may be real but nothing was confirmed by the state or county and the source of any data also remains unconfirmed.
Update: And Then It Was Gone?
At last check this morning, the listing appears to have been totally removed from the forum. Did this site’s questions make the seller nervous or re-think their listing? DataBreaches has no idea, but if the state or county ever get in touch, DataBreaches will provide them with copies of the screencaps as originally posted by the seller.
Update of June 21: DataBreaches received an acknowledgement and thanks from the HCBE webmaster account who says the information had been passed along to their IT department to investigate.