The U.K.’s Royal Mail was the victim of a cyberattack that significantly impacted international delivery services. But was this attack the work of LockBit 3.0 or not?
Those who saw the ransom note said the links in the note pointed to LockBit’s leak site and their chat negotiation site. But as Bleeping Computer reported, the “decryptor ID” to login to the negotiations chat reportedly did not work.
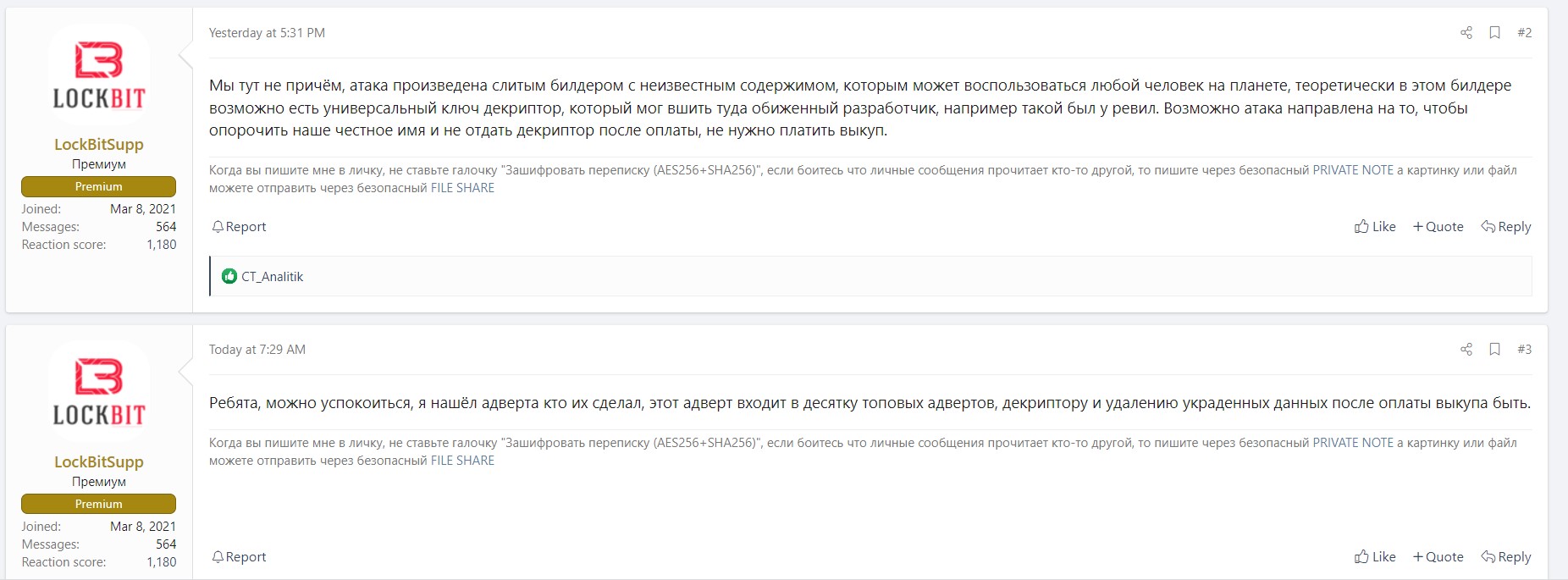
When asked at the time, LockBitSupp, the public face of LockBit, told Bleeping Computer that LockBit was NOT responsible for the attack, and that it was just others using their leaked builder.
What a difference a day or two makes, though.
After repeating the denial on a popular Russian-language forum and saying that since there might not be a real decryptor, there was no reason for Royal Mail to pay any ransom demand, LockBitSupp turned around today and announced that he had identified the affiliate who was responsible for the attack and that he was a “Top 10” affiliate who would provide a decryptor and delete any stolen data if any ransom demand was paid.
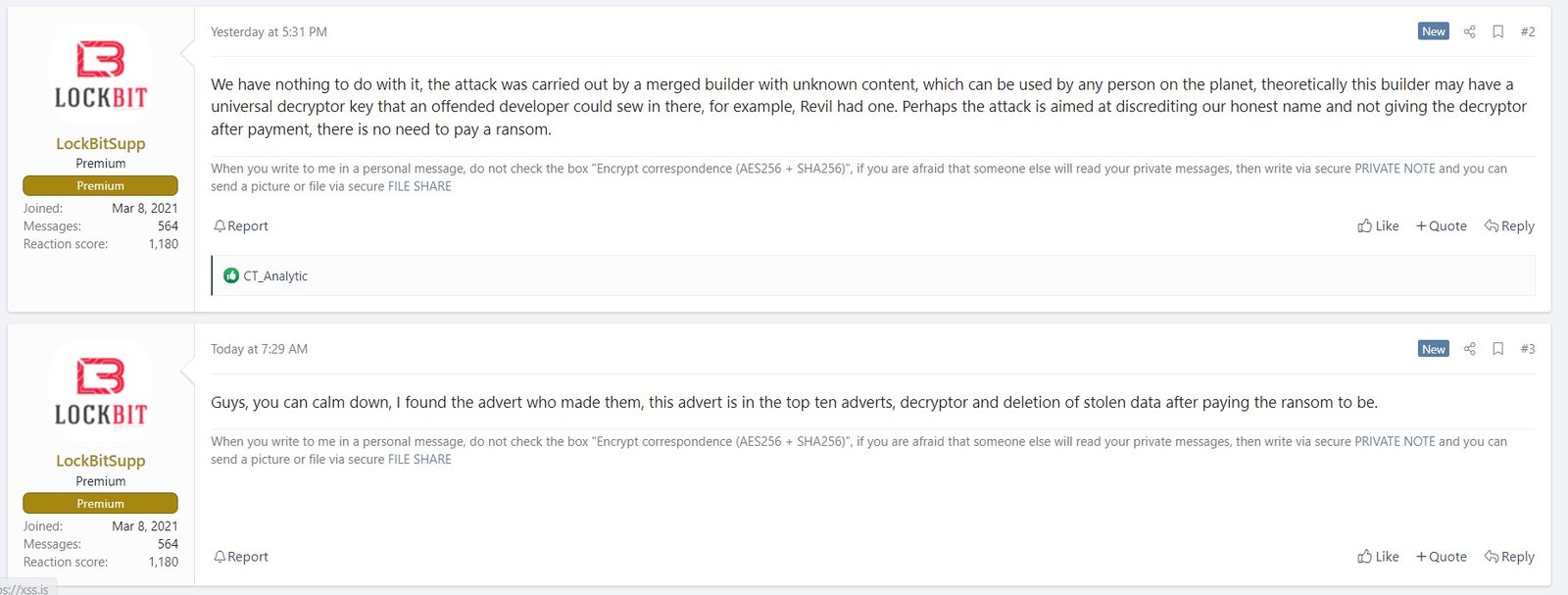
As of publication, the incident does not appear on LockBit’s leak site, and there have been no public claims yet as to how much data might have locked or exfiltrated. Nor is there any information on how much ransom is demanded and whether the Royal Mail is negotiating with the attacker(s) at all.