DataBreaches has received a tip that TIC Hosting Solutions in Romania had a recent data breach affecting customer data. The tipster provided an .SQL database called “Galactic” as an example of data being leaked. The users table included usernames and email addresses, including one for “tichhosting.”
This site was unable to reach TIC Hosting Solutions by email as all attempts to email them bounced back with a 550.5.1.2 error message: “Host unknown (Name server: _dc-mx.b987b9d71670.tichosting.ro.: non-recoverable error)
The firm’s status page also confirms that they are having some problems:

But for how long has TIC Hosting Solutions been experiencing problems? Inspection of the database provided to DataBreaches shows the most recent time stamp was April 22. What occurred on or after that date?
DataBreaches is attempting to get more information and will update this post if more details are received. For now, however, it is important to note that the firm does not appear to have issued any statement confirming or denying any incident.
Update 1: The person who contacted DataBreaches states that the intervention (as they called it) occurred on the morning of April 23. Four servers were reportedly affected and all customers’ data — approximately 4TB — and other databases and systems were reportedly taken.
When asked, the individual would not disclose the vulnerability they claim to have exploited, writing, “I can’t disclose it until they fix it and notify customers about it and also provide them with a full statement about the situation.”
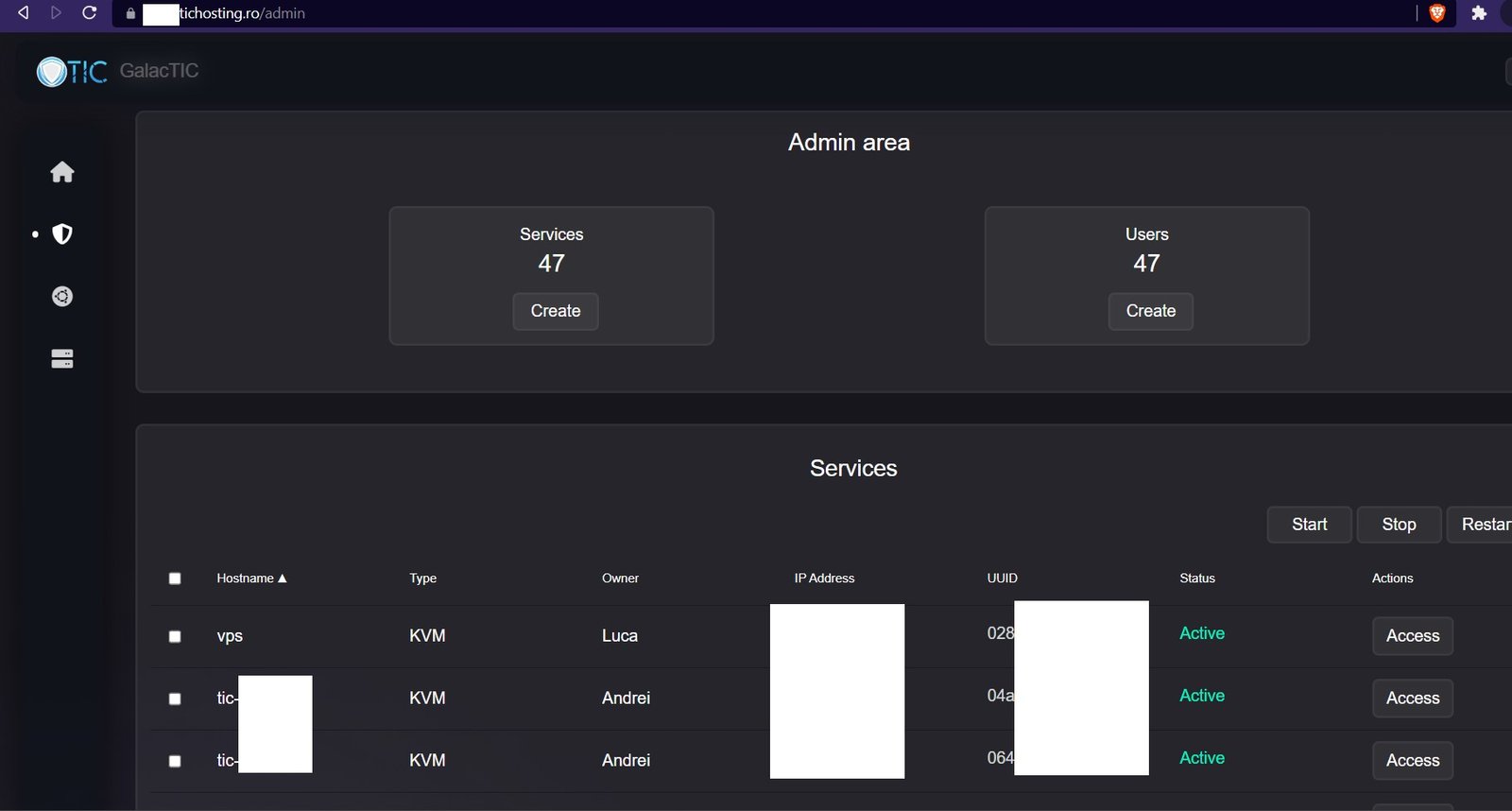
According to this individual, TIC has not responded to the accusations about this incident. “They just said that it was a hardware issue and that they would restore the services in the following days but without the data,” the source wrote. They included a screencap from the firm’s Discord as well as screencaps of GalacTIC admin panels.

The Romanian notices on Discord did not translate particularly well, but they seemed to be reporting a “power shock” that affected storage devices. There did not seem to be any mention of it being a cyberattack. Nor was there any mention of data exfiltration. And according to the source, there were no further notices about the problem and the chats were locked so that people could not respond.
Because DataBreaches was unable to email TIC Hosting Solutions and unable to post on Discord, DataBreaches sent an email to the Gmail address of one of the administrators. The Gmail address had been listed in the GalacTIC users table. No reply was immediately received.
The source says there are over 300 affected customers.
DataBreaches will provide further updates if more information becomes available.
——–
See the update to this published on February 19, 2024.