Although it’s impossible for DataBreaches to really monitor for attacks on medical entities around the world, here are two non-U.S. ones recently spotted that both involve sensitive data.
Plastic Surgery Practice in Brazil
This week, DataBreaches spotted a listing for data from a Brazilian plastic surgery practice. The seller, who calls himself “TheSnake,” claims to have 1.3 TB of files from RobertoPolizzo.com.
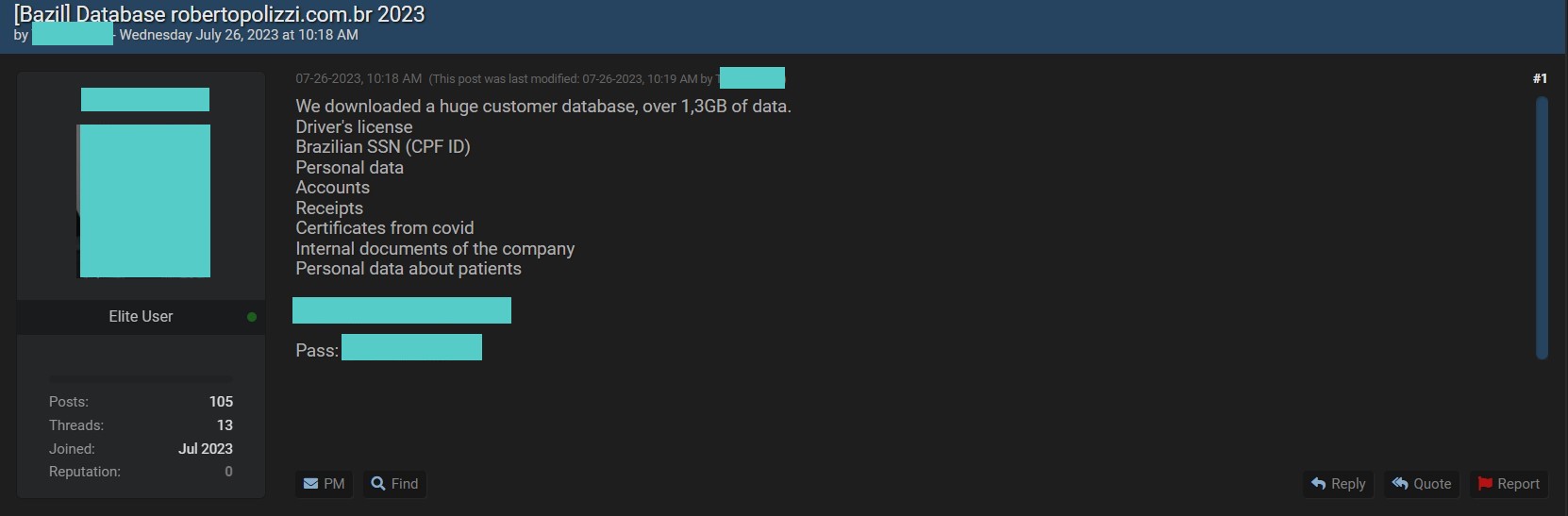
The listing claims that he acquired:
- Driver’s license
- Brazilian SSN (CPF ID)
- Personal data
- Accounts
- Receipts
- Certificates from Covid
- Internal documents of the company; and
- Personal data about patients
In several private messages, DataBreaches obtained more information about the incident. According to TheSnake, he was responsible for hacking them, and when he contacted them, they ignored his contacts.
“They didn’t care when I sent them photos proving that I really have the company’s database too. I thought it was absurd because it was data not only from the client but from the company itself,” he wrote to DataBreaches. “I am planning to launch a ransomware attack on his server and ask for ransom soon,” he added, stating that he also has some self-developed exploits, botnets, and ransomware that he uses in attacks.
A sample of files was uploaded as proof of claims. DataBreaches notes that all the files appeared to be password-protected. DataBreaches sent an email inquiry to Dr. Polizzi yesterday about the claimed attack but received no reply.
There have been a number of recent attacks on plastic surgery sites, with nude photos of patients being uploaded by some attackers as a way of pressuring victims to pay ransom to remove the pictures and medical files from the leak sites. DataBreaches does not know what kinds of patient data may be in the files acquired by TheSnake, but thankfully, he does not appear to be leaking such sensitive material.
Psychiatric Hospital in Lithuania
In a second attack on the medical sector noted this week, DataBreaches spotted an attack on Respublikinė Vilniaus Psichiatrijos Ligoninė (the Republican Vilnius Psychiatric Hospital) in Lithuania by the NoEscape ransomware group.
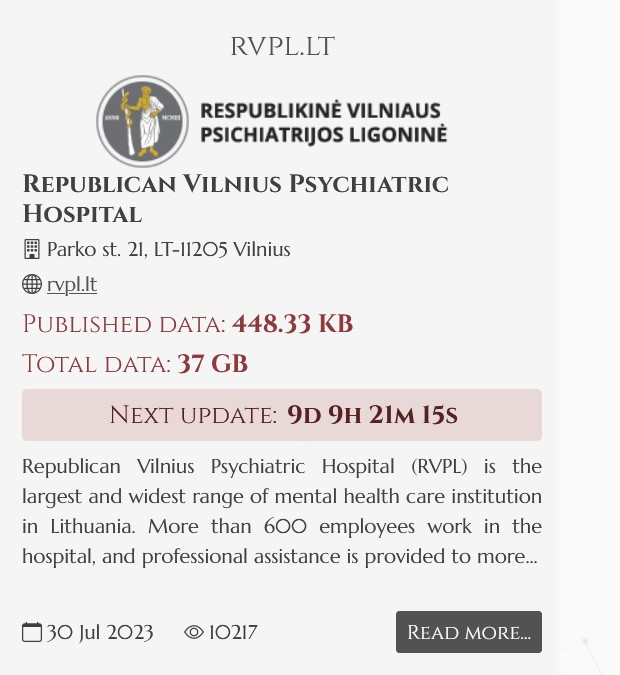
A machine translation of their about page describes the hospital as:
Republican Vilnius Psychiatric Hospital (RVPL) is the largest and widest range of mental health care institution in Lithuania. More than 600 employees work in the hospital, and professional assistance is provided to more than 7,000 people every year. patients.
From emergency care to rehabilitation, from child psychiatry to the treatment of various dementias, from consultations to a comprehensive recovery plan – professional help is available 24 hours a day, seven days a week.
As proof of claims, NoEscape leaked a filetree. The server in question has files that cover a number of years, but according to the attackers, the filetree does not tell the whole story:
The management wants to hide the fact that their servers were encrypted and compromised, this is a bad idea because we have such data as: finances, taxes, personal data of patients, medical records of patients, procedures for admission, treatment and discharge of patients, hundreds of agreements, contracts, documents of employees as well as documents on hiring employees, hygiene passports, health passports, passports of clients and employees, and a lot of other confidential information related to both clients and the company itself.
If you do not get in touch with us as soon as possible, the above data will be published and become public, and your patients and their families may start proceedings that will be followed by lawsuits and very big problems.
The file tree does not contain all the documents we have. When studying the documents that we stolen, were revealed very important and secret documents , for example, about testing new pills on living people and their conclusions…
The countdown clock currently shows 8 days until the next update on the leak site.
So neither of these two attacks has already resulted in the leak of sensitive data but both incidents have the potential to leak or sell personal and sensitive information.
Update: NoEscape subsequently leaked 25.44 GB of files from the psychiatric hospital.