Attacks on the healthcare sector continue, but as this blogger observed in reporting on hacks by thedarkoverlord, it’s often the attackers who first reveal the breaches while the victims may not even reply to inquiries.
AffordaCare Urgent Care Clinic is a walk-in urgent care clinic network in Texas that advertises that they can provide care for most common illnesses and minor injuries. They also have x-ray and diagnostic capabilities. AffordaCare has clinics in two locations in Abilene, one in Early, one in Stephenville, one in Wichita Falls, and one in Big Spring, Texas.
It appears that on February 1, AffordaCare was attacked by Maze Team, who claim to have exfiltrated more than 40 GB of data, including protected health information.
According to the hackers, when AffordaCare didn’t pay the demanded ransom to get a decryption key and to deter the attackers from publicly dumping the stolen data, Maze Team added the clinic to its website where it names its victims who are not cooperating with ransom demands.
For an update on Maze Team’s activities, see our additional reporting today.
As it has done in other cases, Maze Team provided samples of the data they had stolen. The publicly available files included patient insurance claim forms, workers compensation documentation, employee payroll information, and other files. DataBreaches.net has redacted a few of them, below, but the files in the data dump contained patients’ full names, Social Security number, date of birth, diagnosis code, treatment code, patient address and phone number, relevant medical history and reason for visit, billing information, and insurance policy information among the data types. Not all patients had all these types of information in their exposed files.
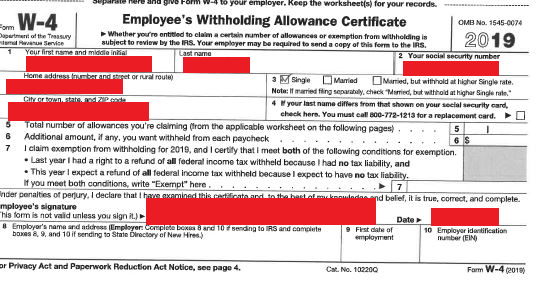
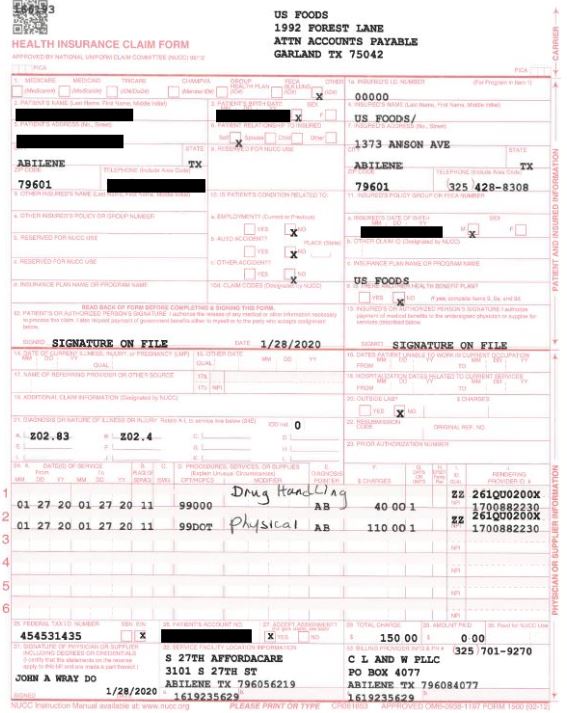

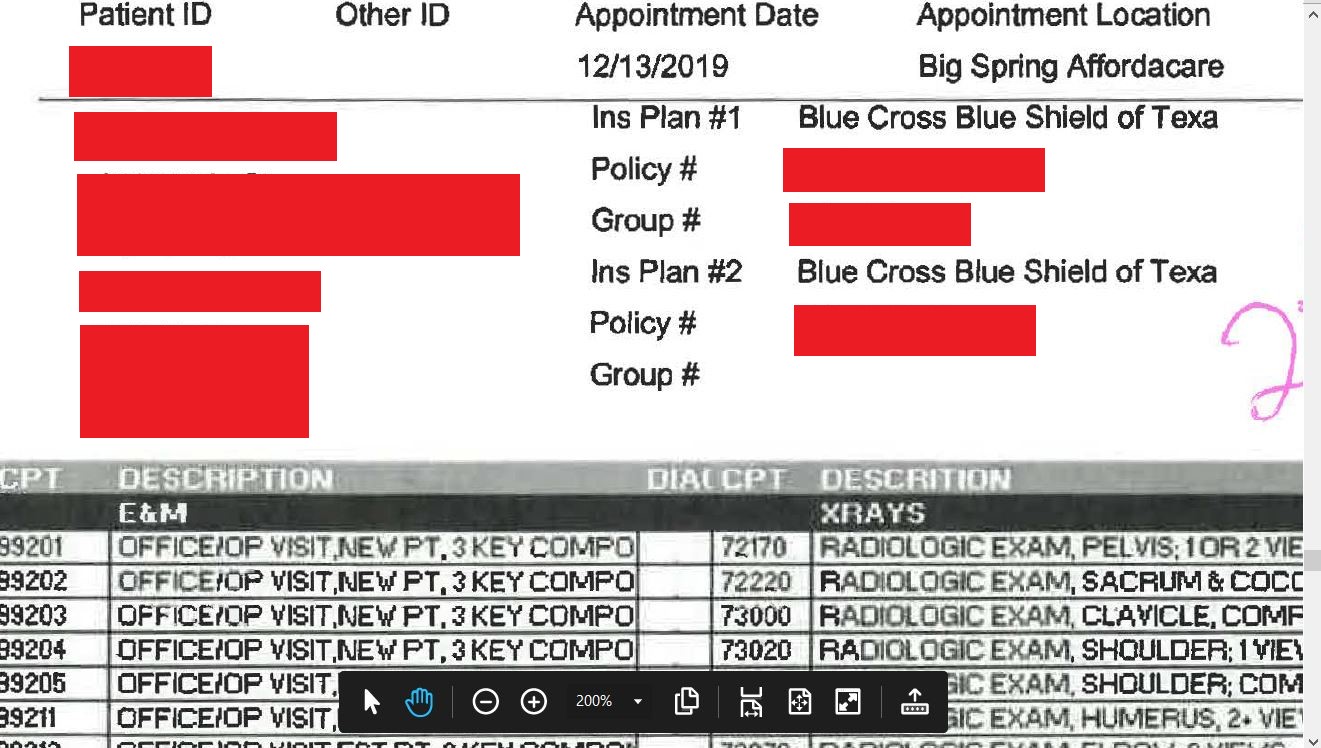
If you were a patient at an AffordaCare urgent care center in Texas prior to February 1, 2020, have you received any notice of any breach? Have you recently become a victim of fraud or identity theft? We’d love to hear from you.
AffordaCare did not respond to inquiries sent to the site about the attack. They continue to update their Facebook account without making any mention at all of a privacy incident. Nor does the breach appear on their website or on HHS’s public breach tool at the time of this publication. With multiple locations, this breach may easily have compromised thousands of patients’ protected health information. We’ll have to wait and see if AffordaCare discloses this publicly and reports it to HHS within the 60 day window.
Update of March 31: AffordaCare reportedly sent notification letters to patients that said that patients’s SSN were not involved. There is no entry on HHS’s breach tool yet with any numbers.
Update of April 3: After AffordaCare issued a statement claiming that no SSN were involved — a statement that was inconsistent with the data that this site saw and reported upon and that Emisoft also commented on — AffordaCare revised their notification. The statement on their site now reads:
Affordacare’s servers contained confidential information to include the patient’s full name, address, telephone number, date of birth, age, date of visit, location of visit, reason for visit, insurance plan provider, insurance plan policy number, insurance group number, treatment codes and descriptions, and brief comments from the health care provider. The breach also may have affected Social Security numbers, diagnosis codes, relevant medical history, and other health care information. Affordacare continues to investigate the scope of information affected.
But AffordaCare is not the only urgent care clinic that this site is watching for follow-up. DataBreaches.net was also recently made aware of another urgent care center that also appears to have been attacked.
Advanced Urgent Care of the Florida Keys
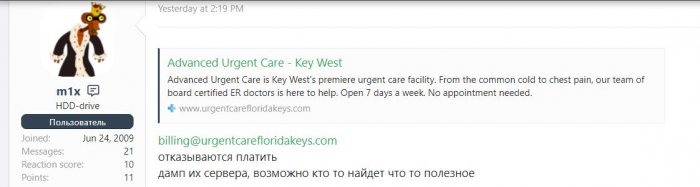
Advanced Urgent Care of the Florida Keys. Upon discovery of another urgent care facility being attacked, DataBreaches.net reached out to Maze Team to inquire whether this center was also one of their victims. Maze Team replied that this was not their attack.
We might know more about this one if it had been by Maze Team, as we currently have very little information on this attack. Data from the attack was posted on a Russian-language forum in a thread that translates to “Malicious Defaulters.” From that subject line and a comment by the poster that Advanced Urgent Care of Florida Keys “refuse to pay,” it sounds like a ransomware attack, but that has yet to be confirmed. The poster added, “dump of their server, maybe someone will find something useful” (Google translation).
The data, made freely available on a popular file-sharing site, contained more than 14,000 patients’ personal information. For some of the patients, there were numerous scans of patient records. In most cases, these were scans of reports that included some handwritten notes and results with the patients’ personal information, medical history, reason for testing or visit, and more.
As with the Texas group, the Florida practice’s dump contained a wealth of protected health information as well as billing information.
One of the folders contained spread sheets listing patient first and last names, phone numbers, email addresses, and co-pay status on bills.
Other “export” spread sheets listed patients by their medical record numbers but listed their insurer, date of service, diagnosis (in text, not coded number), CPT code, and information on co-pay, etc.


Advanced Urgent Care of the Florida Keys was sent several inquiries about the attack and data dump but did not reply at all.
Based on the timestamps and filenames, the data appear to have been exfiltrated on or about March 1 of this year, so this is a recent attack and we may not see any notice or entry on HHS’s public breach tool for a while.