While many were looking forward to the Labor Day holiday weekend, the IT department at OakBend Medical Center learned they had been hit with a ransomware attack. The center is still trying to recover.
In a notice on its website, the Texas medical center disclosed that after being hit by ransomware on September 1, it promptly took all systems offline, placed them in lockdown mode, and referred the attack to the FBI, CYD, and the Ft. Bend County Government Cyberteam to investigate. When experts from Dell, Microsoft, Malware Protects, and their IT staff cleared them to start rebuilding their system, they started rebuilding it.
Quick Facts: OakBend, which describes itself as the last remaining independent nonprofit hospital in the Greater Houston Area, has 450 physicians, more than 1200 employees, 274 beds, and more than 50 locations. On an annual basis, they see more than 8,500 inpatients, 100,000 outpatients, and 40,000 Emergency Room visits.
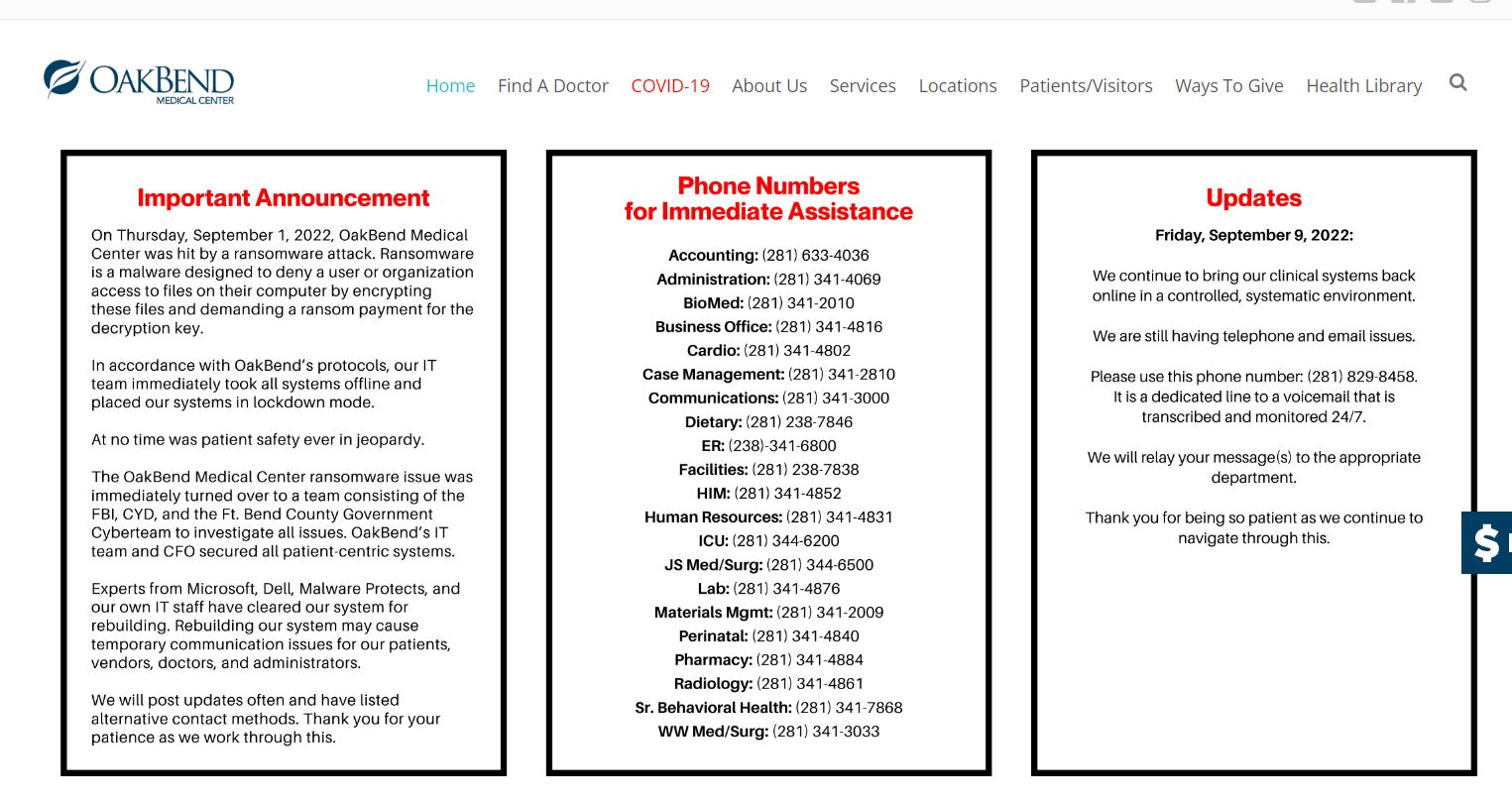
As of September 9, OakBend reported they were still in the process of rebuilding and that phones and email were still impacted. Alternative phone numbers were posted prominently to assist patients in reaching them.
Of note, their notice stated, “At no time was patient safety ever in jeopardy.”
Patient safety may not have been jeopardized, but the privacy and confidentiality of some of their patient data and employee/personnel information are now in the hands of people who claim they will start leaking it publicly next week.
Although OakBend’s notice does not name the ransomware group responsible for the attack, Daixin Team contacted DataBabreaches on Friday, claiming responsibility for the attack on OakBend Medical Center and OakBend Medical Group. DataBreaches previewed a file list showing 258 directories with 6,051 files. Daixin claims they exfiltrated approximately 3.5 GB of data, including 1.2M records with patient and employee data.
While OakBend Medical Center’s site displays a notice of the attack, OakBend Medical Group‘s website does not show any notification of any breach. DataBreaches sent an inquiry asking them about Daixin’s claim, but no reply has been received.

In addition to the file directory, Daixin provided this site with a sample of patient records. The sample, a .csv file, had 2000 rows. Some patients had more than one record, so the sample did not include data from 2,000 patients. The types of protected health information included approximately 90 data fields, although not every field had data. Some of the fields were: Master Patient ID, Name, Gender, Date of Birth, BSA, Ideal Body Weight, Height, Weight, Social Security Number, BMI, Religion, Pregnancy Status, Smoker, Address, Last Admission Date, Last Discharge Date, Date of Last Visit, Medical Record Number, Physician, Visit Status/Debt, and Medical/Presenting Complaint (those are just some of the fields). Everything was plain text, including full Social Security Numbers, date of birth, name, and address.

According to Daixin, shortly after the encryption was finished, someone who appeared to be an employee of the medical center entered Daixin’s chat. Daixin explained to the person what had just happened and advised them to contact management. As Daixin informed DataBreaches, OakBend knew immediately that Daixin Team had their data, but according to Daixin, once the FBI got involved, OakBend did not return to the chat.
“Possible the FBI not worry about the possible publication of more than a million personal data of USA citizens and definitely don’t worry about OakBend Medical business,” Daixin wrote to DataBreaches.
In follow-up communications with Daixin, DataBreaches inquired about the medical center’s statement that they were rebuilding their system and asked whether Daixin had also encrypted the center’s backup(s). Their spokesperson replied that Daixin had encrypted the medical center’s backups, but “Perhaps they had more backups that we didn’t notice, or they are thinking of restoring the systems from the clear page. If there were good backups, they would have restored everything long ago.” That comment seems a bit speculative because OakBend did not indicate when they were first able to begin rebuilding.
Although Daixin did not provide samples of employee data, they claim to have employees’ information, including full Social Security Numbers. Because OakBend’s email system is still not restored and DataBreaches did not want to tie up their alternate phone system with a non-urgent inquiry, we have not yet reached out to OakBend Medical Center. If OakBend Medical Group responds to our question, this post will be updated.
About Daixin Team
OakBend Medical Center is the third victim publicly revealed by Daixin Team and the second healthcare entity. DataBreaches does not know how many other healthcare entities they may have hit who paid their ransom demands.
Daixin first appeared publicly in June when they contacted DataBreaches to claim an attack on Fitzgibbon Hospital in Missouri. The hospital never responded to inquiries about the attack and, more than two months later, still has not posted any notice of the breach on its website. It is unclear whether they might still be attempting to recover from the attack or if they have fully recovered. Although it may take some entities time to determine who needs to be notified, given that the data was dumped publicly and anyone could obtain and misuse it, it is especially important to notify promptly. DataBreaches sent a follow-up inquiry to Fitzgibbon Hospital yesterday, requesting a copy of any breach notification letter they may have sent and asking them if they have notified HHS yet. Once again, they did not reply.
The second victim that Daixin named publicly, ista international, reportedly had thousands of its servers encrypted. Although ista claimed that they had not negotiated with Daixin, Daixin provided DataBreaches with chat logs showing exactly how much ista had offered during negotiations.
DataBreaches has not found any analyses or reports on Daixin Team. Based on the three victims DataBreaches has some knowledge about, Daixin follows the double extortion model of exfiltrating data and encrypting the victim’s system. They also encrypt any connected backups to make it more likely that victims will need to pay for a decryptor key. When they add a victim to their leak site, they will likely start with a file list as proof. Unlike groups that then give victims more time to pay, Daixin Team appears to move more quickly. Once they announce a victim, full data leaks start shortly after that.
Unlike many other groups, Daixin claims they have attacked Russian or CIS targets.
Given Daixin Team’s risk to the healthcare sector, DataBreaches would not be surprised to see a joint CSA advisory about them at some point.
Really interesting article about what is relatively a new Ransomware Operator. Posted a direct link to this on my website. 🙂