Today’s episode of Incident Response Fail involves a cybersecurity professional/bug bounty hunter, Mohamed Suwaiz, and a driver training company in Texas, Smith System, that seemed to stubbornly resist his efforts to alert them to a data leak.
Although Suwaiz (@Msuwaiz on Twitter) describes himself as being motivated by bug bounties, when there’s no bounty to be had, he just gives information that he finds to companies to help them secure their data.
A few days after we first met online while I was investigating the Leon County Schools case, Suwaiz reached out to me to tell me that he needed to talk to me.
“@drive_different is having huge data leak,” he told me. He had already tried unsuccessfully to contact them via emails, Facebook, Twitter, and by contacting an intermediary to help him call the CTO, he explained. Calling from his part of the world is not easy, he said, so he had enlisted the help of someone who might help him get through.
So far, all of his attempts had failed to produce any results.
But it was his interaction with Smith System’s Twitter team (@drive_different) that blew my mind when he showed me the DM chat log:
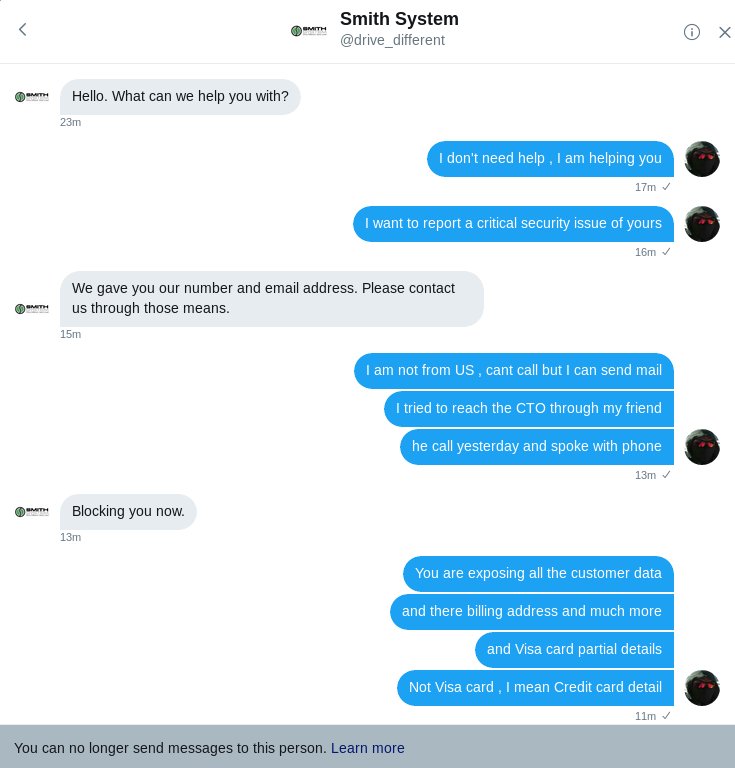
drive_different: Hello. What can we help you with?
Msuwaiz: I don’t need help. I am helping you. I want to report a critical security issue of yours.
drive_different: We gave you our number and email address. Please contact us through those means.
Msuwaiz: I am not from US, cant call but I can send mail. I tried to reach the CTO through my friend. he call yesterday and spoke with phone
drive_different: Blocking you now.
Msuwaiz: You are exposing all the customer data and there billing address and much more and Visa card partial details. Not Visa card, I mean Credit card detail
And that’s when Suwaiz got a message from Twitter: “You can no longer send messages to this person. Learn more.”
I’m not sure it was Suwaiz who needed to “Learn more,” as much as the company who blocked him.
Someone reaches out to give you helpful info that you’ve got a data breach or leak, and you unhelpfully tell them that they have to contact you another way? Even after they tell you that they tried one of those ways and can’t use the other way?
Why hadn’t Smith System responded to any of the emails that Suwaiz had already sent by then? What if he had given up at that point? Their response risked losing helpful information.
Are you reading this, Federal Trade Commission? I hope you are.
If someone contacts you to tell you that you have a data leak, get some information and find out how to reach them to follow up. Then pass the information along or follow your IR protocols to escalate the message. And I know, I shouldn’t have needed to even write that, but Smith System’s Twitter team not only failed to gather information from Suwaiz, but they actually blocked him from telling them more. Unbelievable.
Frankly, I would not have blamed Suwaiz if he had just said “screw it” at that point and not pursued it. But he seems to be a good guy, and had reached out to me to see if I could let the company know they had a leak. It was already clear to him that there was no bug bounty to be had, yet he was still spending his time (and now mine) trying to help a company that idiotically refused to gather some information and then rudely blocked him.
So I asked Suwaiz to give me some data that I could use as proof when I reached out to the company. He gave me a number of carefully redacted screenshots and the IP addresses where the data were exposed. On March 18, I called Smith System. I also sent them a detailed email with some proof and the IP addresses. I will not be disclosing any of the data or details here.
In my email, I asked Smith System to acknowledge receipt of my email and to let me know when the data were secured.
Smith System did not respond to my voicemail. Smith System did not respond to my email, either, although it appears that they secured the data after I notified them.
Incident response needs to make it easy for people to notify you of a problem. It should also include that “response” bit – including acknowledging any notification. Why haven’t entities already learned that?
What is interesting is that they ALL COME to you to try and get a Better result. Based on some of your reports, it sounds like you hit a brick wall on many and there are some where you better results than others.
What is the secret? Just going in and not caring how you get it done? 🙂
“No good deed goes unpunished”
That bullshit axiom needs to change, and soon.
Watch for a story I’ll probably be posting on Monday about hassles in notifications.
Only a complete idiot would take such contacts seriously. I am shocked that this website promotes people like MSuwaiz who is a complete hoaxer.
How do you know a contact is not to be taken seriously if you don’t check into what they provide or say?
Look at Panera as a recent example… they dismissed reports of their vulnerability as a scam. And the docs on Long Island who didn’t respond to Upguard or even return my phone call….
So I’m not sure who the complete idiots are. I tend to think it’s those who don’t investigate or try to verify or disconfirm. I understand skepticism but you still need to check.
As to MSuwaiz, well, his info turned out to be accurate in this case and in one other case that I’m aware of. I don’t have any other info on him.